Seizing the Opportunities of Big Data
A good place to start with data analytics is to subscribe to reports on data trends, or to a trends-based web service. These services, such as Microsoft Insights, can provide valuable research data relevant to your business operations. Big data allows researchers to collect and analyze various industry trends and patterns, draw conclusions, and publish…

Data for Democracy Project
Monitoring Elections The Data for Democracy Project aims to identify and recommend strategies, tools, and technology to protect democratic processes and systems from social media misinformation and disinformation. By creating a technology solution that permits observers to monitor election interference, we offer a unique and bipartisan approach to election monitoring. Built by experts in technology,…

Best-Practice Data Transfers for Canadian Companies – III – Vendor Contracts
PREPARING FOR DATA TRANSFER – CLAUSES FOR VENDOR CONTRACTS A three-part series from KI Design: Part I: Data Outsourcing Part II: Cross-border Data Transfers Part III: Preparing for Data Transfer – Clauses for Vendor Contracts The following guidelines are best-practice recommendations for ensuring that transferred data is processed in compliance with standard regulatory privacy laws. While a…

Best-Practice Data Transfers for Canadian Companies – Part II
CROSS-BORDER DATA TRANSFERS A three-part series from KI Design: Part I: Data Outsourcing , Part II: Cross-border Data Transfers, Part III: Preparing for Data Transfer – Clauses for Vendor Contracts When personal information (PI) is moved across federal or provincial boundaries in the course of commercial activity, it’s considered a cross-border data transfer. Transferring data brings…

Best-Practice Data Transfers for Canadian Companies – I – Outsourcing
DATA OUTSOURCING In our digitally interconnected world, most organizations that handle personal information will transfer it to a third party at some stage of the data life cycle. Your company may send personal information (PI) to an external service provider such as PayPal to process customer payments – that’s a data transfer. Perhaps you hired…

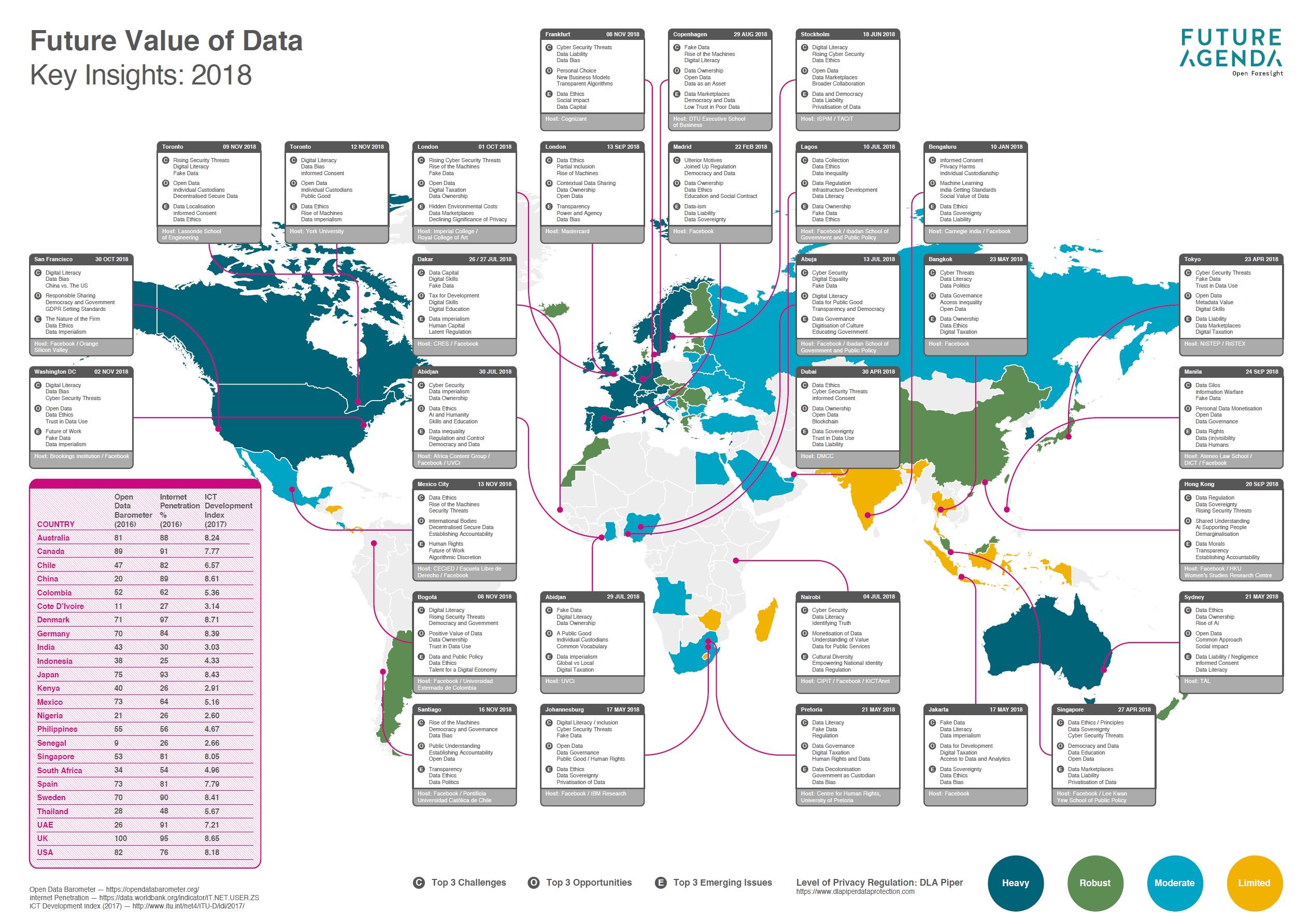
Future of Data
Infographic representing key issues concerning future of data broken by country. Link to source: Future of Data

Parliament Responds to the Standing Committee’s Report on Access to Information, Privacy and Ethics
The Honourable Navdeep Bains, P.C., M.P. extends his gratitude for report of the Standing Committee on Access to Information, Privacy and Ethics titled, Privacy by Design: Review of the Personal Information Protection and Electronic Documents Act. His response encompasses the following summary. He shows his appreciation for the OPC and other witnesses that supported this study and…

Designing Smart Cities – A Design Thinking Approach
Privacy, Data Management, and Risk Mitigation While no clear definition or requirements of a “smart city” exist, the general consensus is that it is an innovative development initiative that combines urban planning with creative digital infrastructure. Areas of focus often include reducing traffic congestion, improving sustainable energy use, and making public spaces more accessible and…

Can big Data be wrong – An election post mortem
Well that’s a good question, everyone is asking today what happened with the elections. Thinking that all that we knew and heard from media outlets was wrong. Big Data is subject to a few simple rules which often get ignored. When the next election or event comes along, there is one thing to remember. Big Data has…