Do ‘Contact Tracing Apps’ need a Privacy Test?
The Coronavirus continues to cause serious damage to humanity: loss of life, employment, and economic opportunity. In an effort to restart economic activity, governments at every level, local, regional, and national, have been working on a phased approach to re-opening. However, with re-opening comes a substantial risk of outbreaks. Epidemiological studies are showing that shutdowns have…

Blackbaud breach – Executive Options in light of Reports to OPC & ICO
Three Executive Actions to help mitigate further risk If your company leverages Blackbaud CRM – this article will provide you of three actions that will help mitigate risk. Blackbaud a reputable company that offers a customer relationship management system has been hit and paid off ransomware. According to G2, Blackbaud CRM is a cloud fundraising and…

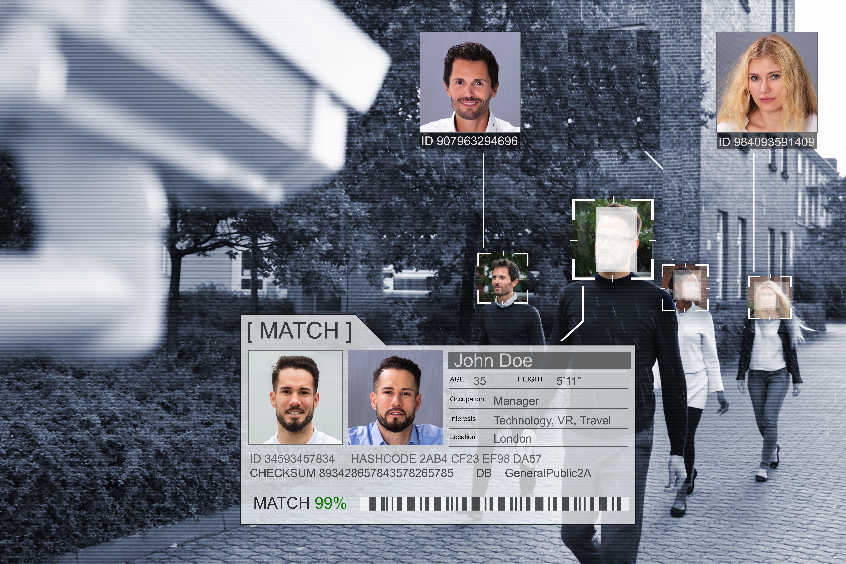
Police use of AI-based facial recognition – Privacy threats and opportunities !!
This article describes the issue of Police use of AI-based facial recognition technology, discusses why it poses a problem, describes the methodology of assessment, and proposes a solution The CBC reported on March 3[1] that the federal privacy watchdog in Canada and three of its provincial counterparts will jointly investigate police use of facial-recognition technology…

Best-Practice Data Transfers for Canadian Companies – III – Vendor Contracts
PREPARING FOR DATA TRANSFER – CLAUSES FOR VENDOR CONTRACTS A three-part series from KI Design: Part I: Data Outsourcing Part II: Cross-border Data Transfers Part III: Preparing for Data Transfer – Clauses for Vendor Contracts The following guidelines are best-practice recommendations for ensuring that transferred data is processed in compliance with standard regulatory privacy laws. While a…

Best-Practice Data Transfers for Canadian Companies – Part II
CROSS-BORDER DATA TRANSFERS A three-part series from KI Design: Part I: Data Outsourcing , Part II: Cross-border Data Transfers, Part III: Preparing for Data Transfer – Clauses for Vendor Contracts When personal information (PI) is moved across federal or provincial boundaries in the course of commercial activity, it’s considered a cross-border data transfer. Transferring data brings…

Best-Practice Data Transfers for Canadian Companies – I – Outsourcing
DATA OUTSOURCING In our digitally interconnected world, most organizations that handle personal information will transfer it to a third party at some stage of the data life cycle. Your company may send personal information (PI) to an external service provider such as PayPal to process customer payments – that’s a data transfer. Perhaps you hired…

“False Light” – Canada’s Newest Tort
A tort recognized by the Ontario Superior Court of Justice last month expands privacy protections for Canadians by adopting a well-established US cause of action. Torts are an essential element of common law. A tort is a wrongful act or injury that leads to physical, emotional, or financial damage to a person, for which another…

Privacy in Design: A Practical Guide to Corporate Compliance
A series of articles offering a sneak peek into my e-book, Privacy in Design: A Practical Guide to Corporate Compliance.

Urban Data Responsibility – The Battle for TorontotechUrban Data Responsibility – The Battle for Toronto
The initial excitement over Alphabet’s SmartCity may be dwindling out of the perception that the tech giant will use the new development in the Harbourfront to collect personal data. The special attention given by interest groups to a project that actually has engaged the public and shown good faith may be giving companies the wrong lesson: Don’t…

Smart Privacy Auditing – An Ontario Healthcare Case Study
IPCS Smart Privacy Auditing Seminar On September 13, Dr. Waël Hassan, was a panelist at the Innovation Procurement Case Study Seminar on Smart Privacy Auditing, hosted by Mackenzie Innovation Institute (Mi2) and the Ontario Centres of Excellence (OCE). The seminar attracted leaders from the healthcare sector, the private information and technology industry, and privacy authorities.…

Are Malls “Grasping at Straws”?
Cadillac Fairview is tracking the public by using facial recognition technology !! The news of privacy commissioners of Canada and Alberta launching an investigation into facial recognition technology used at Cadillac Fairview, did not come as a surprise to many. The investigation was initiated by Commissioner Daniel Therrien in the wake of numerous media reports that…

Parliament Responds to the Standing Committee’s Report on Access to Information, Privacy and Ethics
The Honourable Navdeep Bains, P.C., M.P. extends his gratitude for report of the Standing Committee on Access to Information, Privacy and Ethics titled, Privacy by Design: Review of the Personal Information Protection and Electronic Documents Act. His response encompasses the following summary. He shows his appreciation for the OPC and other witnesses that supported this study and…